THM - Biohazard
Target IP: 10.10.190.138
Enumeration
Open Ports
- Port 21 - FTP
- Port 22 - SSH
- Port 80 - HTTP
Enumerating the Web Server
Upon accessing the website, we are given the base site
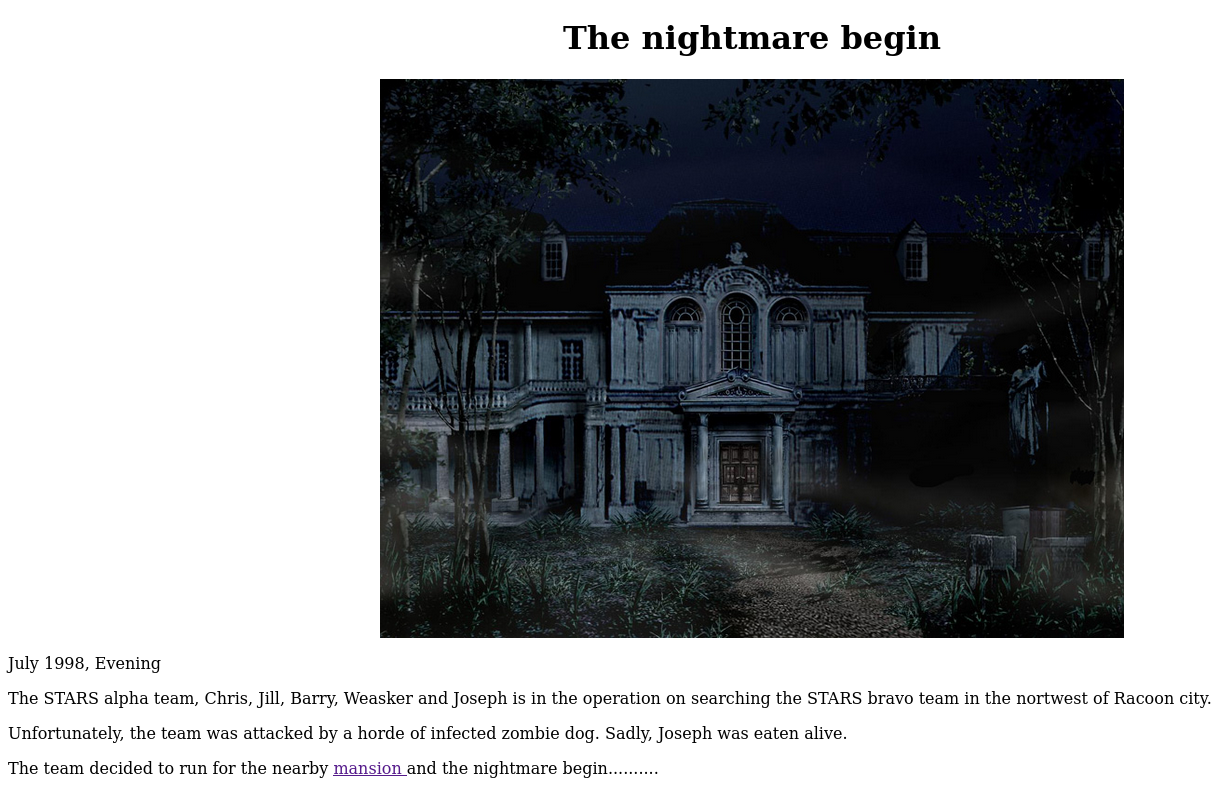
We then click the link and are given this site

In the source code we find:
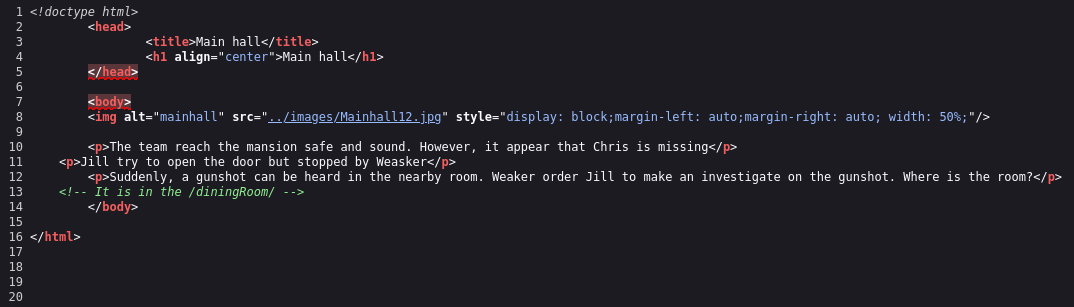
Upon accessing this page we find:
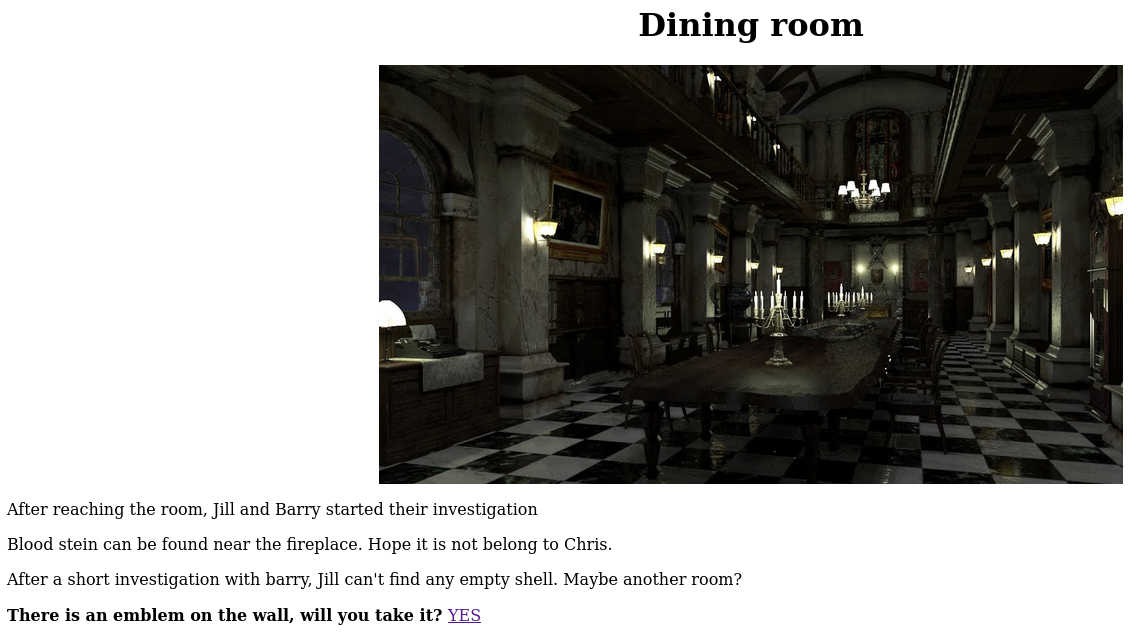
By clicking the link we find an emblem:

After looking in the source code for the dining room we find a base64 encoded string:
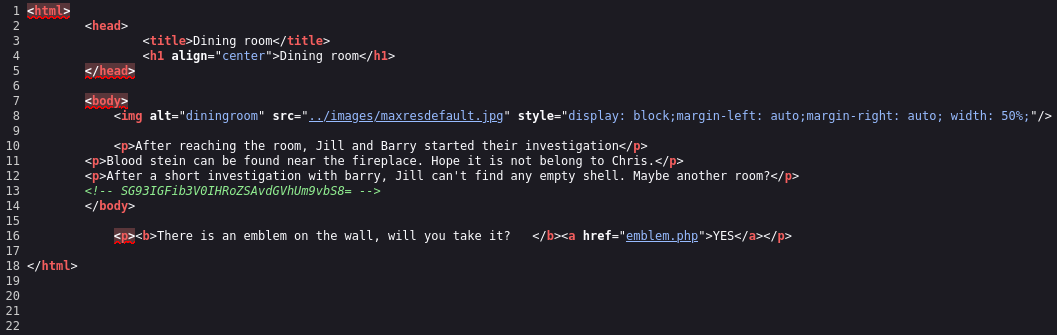
After decoding the string we obtain:

By travelling to this page, this is what we get:
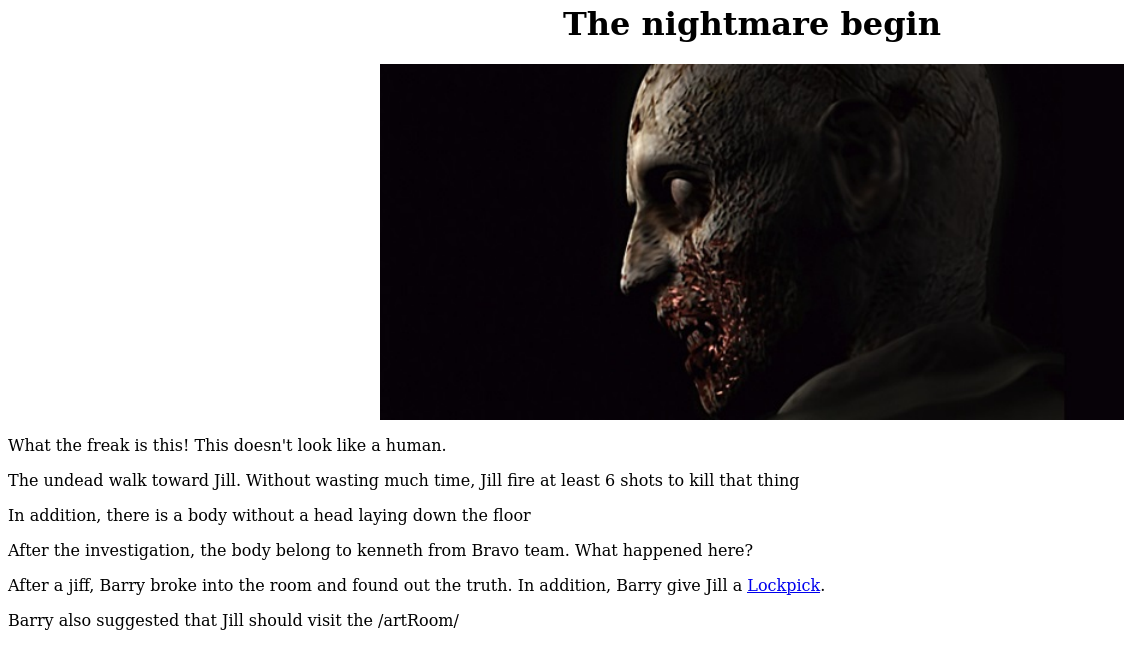
By clicking the link we receive the lockpick flag:
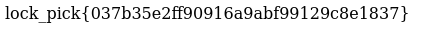
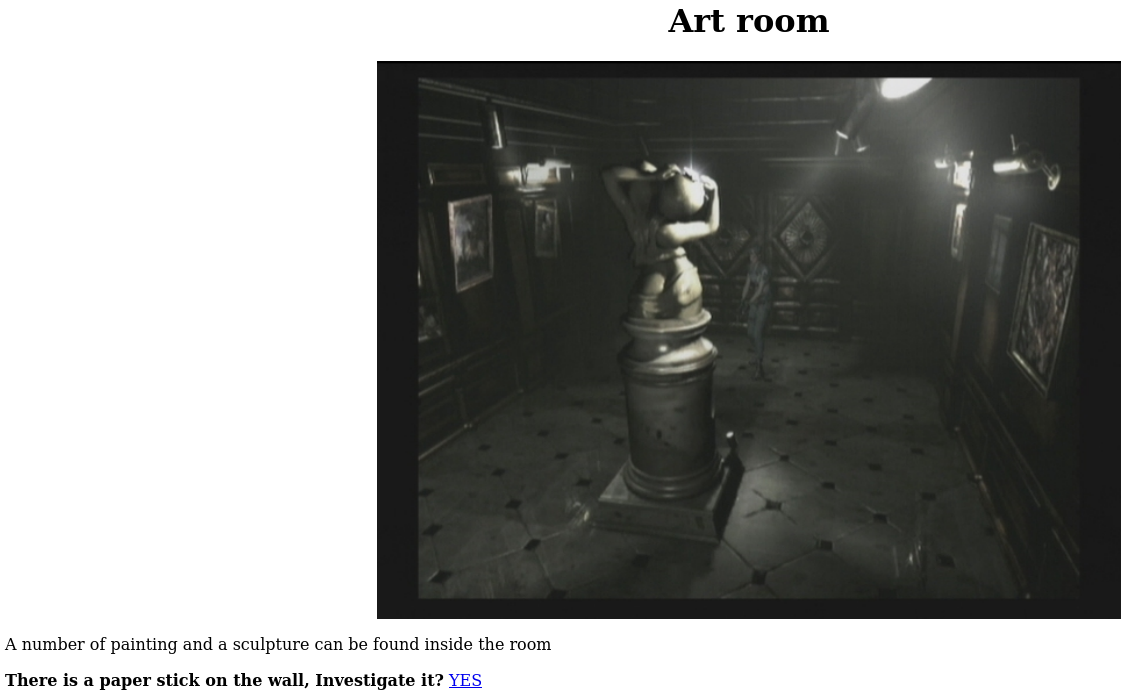
The page suggests that we visit the art Room, upon visiting the page we see:
We are given a link to click after clicking it we are given a map of the website:

We begin to go to each new room, by going to the barRoom we discover the fact we need to use a lockpick we obtained earlier.

Upon entering the lockpick we enter the bar room:
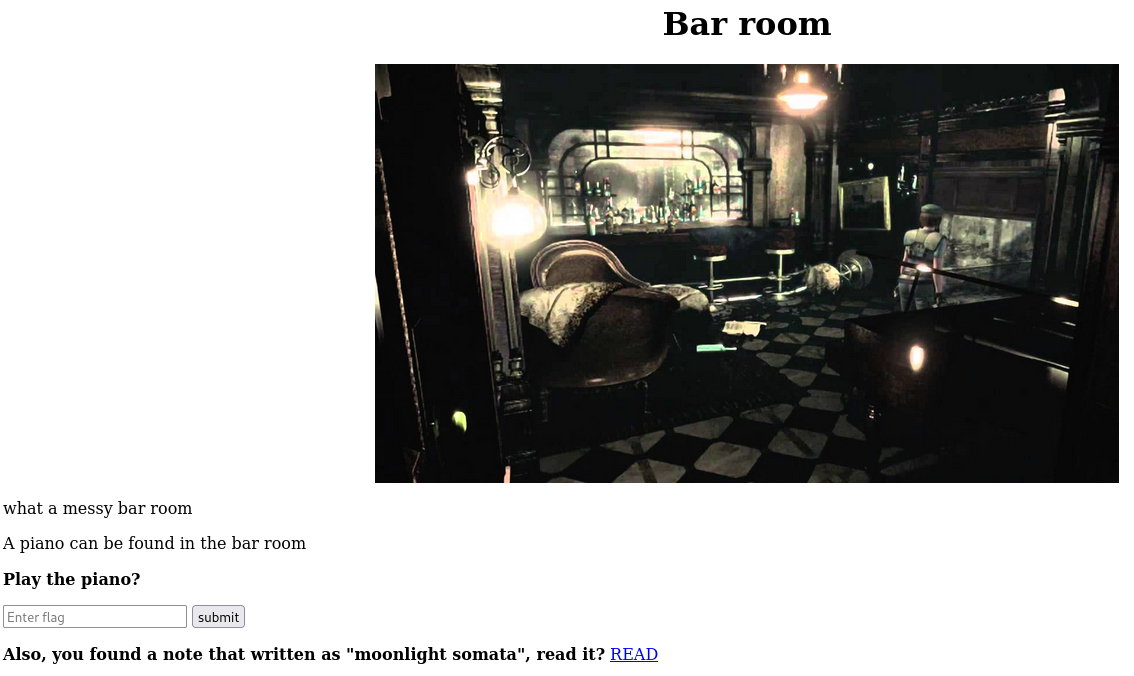
There is a link to read moonlight somata, clicking this link we go a page with a code:
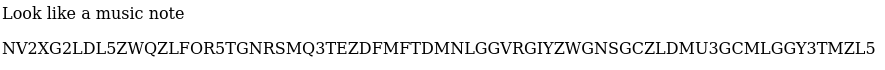
This is a base32 string when converted we receive:
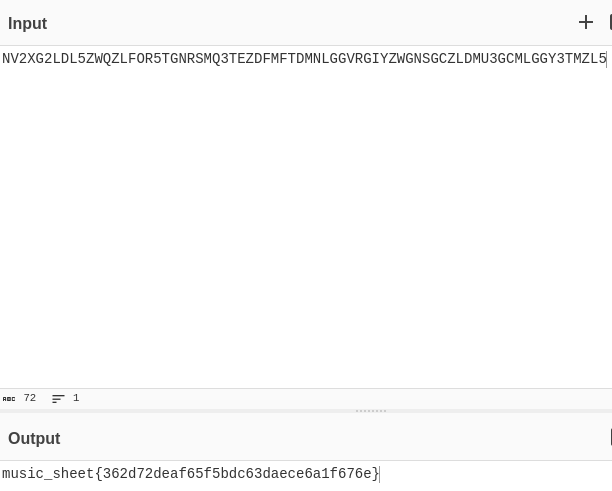
Upon entering this sheet in the bar room we enter this page:

There is a link, once clicked we receive the emblem:

We are instructed to place this in an emblem slot on a previous page, we discover that by placing this emblem in the dining room we receive a code:
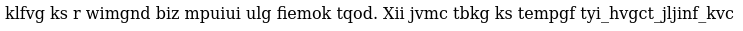
I believe this is a vignere cipher but I do not know the key. I refresh the secret bar page and place the original emblem in the slot that the gold emblem used to be, there we receive a name:
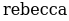
I believe this is the vignere cipher's key upon entering it into the decoder we find this:
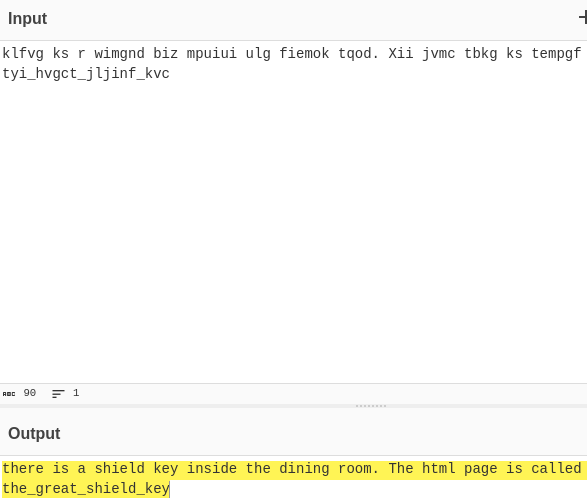
By going to the page (/diningRoom/thegreatshieldkey.html) we find this:
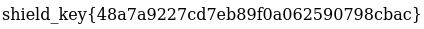
We then go to two different rooms starting with the armor room where a shield symbol is embedded into the door:

Upon entering the shieldkey we get:

Upon clicking the link we get:
This is one part of a multipart cipher. We will continue to the next room before decoding the crests. We will go to the attic:

Entering the shieldkey we get:

Reading the note we get:
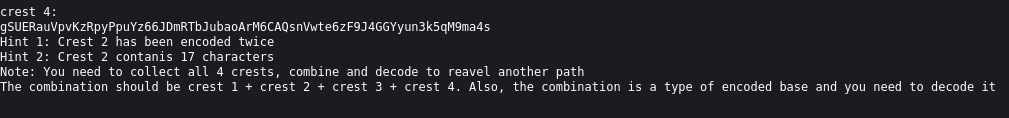
There seems to be two more crests we will go back to the rooms we missed on the map, we will first head to the DiningRoom2F, here we find:

Checking the source code we find some encrypted text:
This encrypted text is encoded using ROT13 by decrypting we receive:
Going it the link we receive:

We then go to the tiger status room:
Placing the gem into the tiger's eye we get:

Looking in the gallery Room we find:
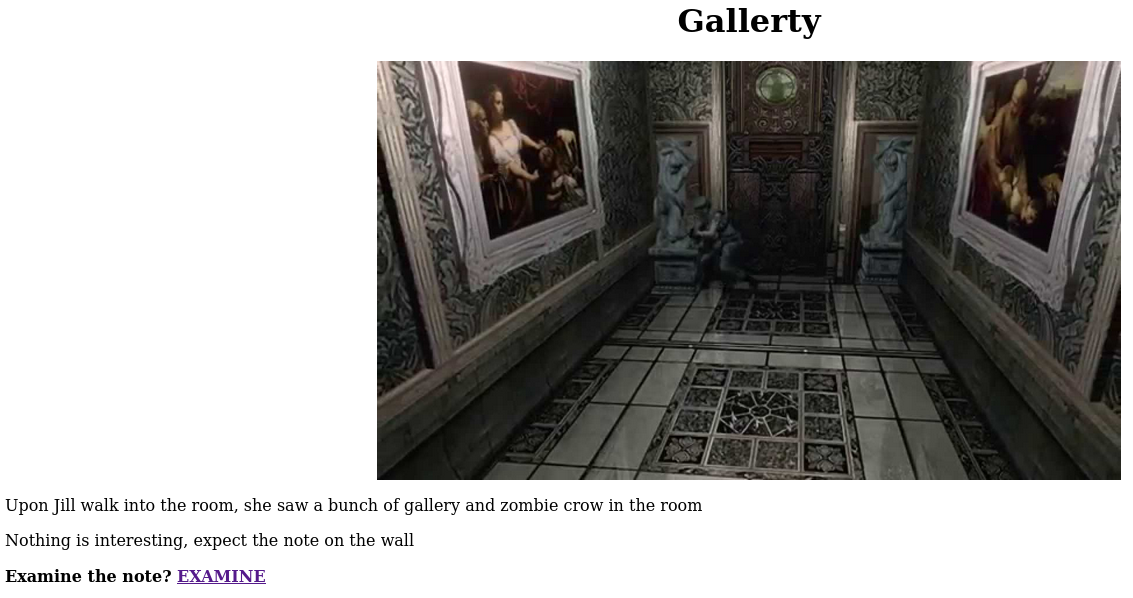
Following the link, we find the final crest:
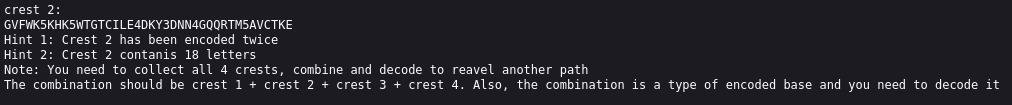
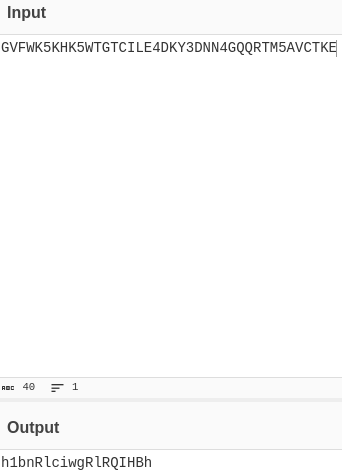
By decoding all of the crests we get:

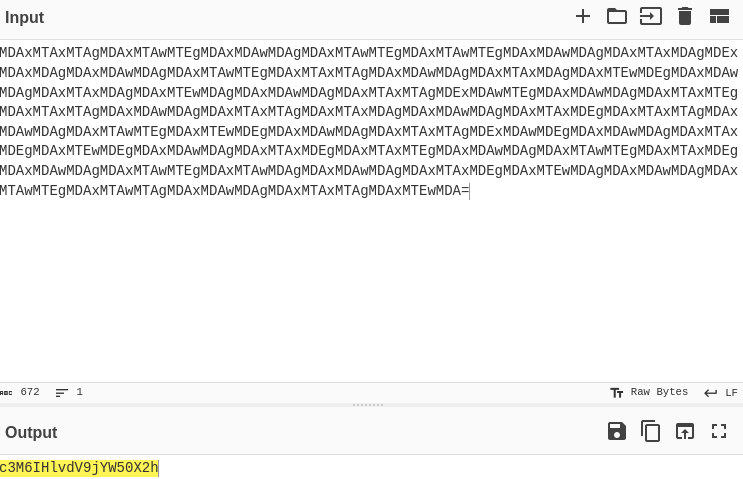
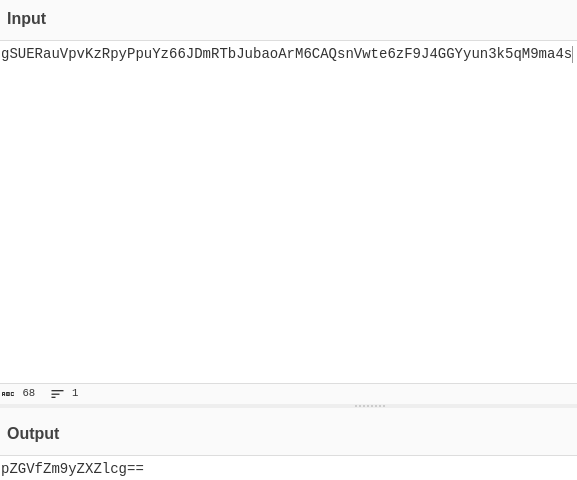
By putting them together and decoding we get:
Enumerating FTP
Upon entering the FTP given the above credentials we see these files:
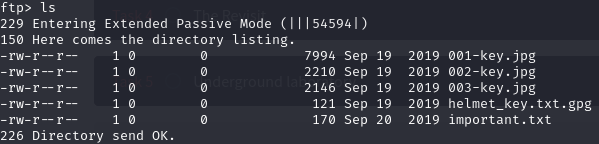
Once we get all of the files from FTP we can analyse each one. We will start with seeing what important.txt says:
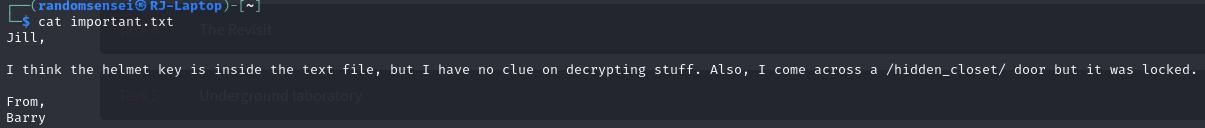
There seems to be a /hiddencloset/ webpage but it also needs the helmetkey.
Now looking at the three keys we were given, there doesn't seem to be anything visually worth looking at but we will first check using steghide to see if there are any hidden files located within the image. Upon doing this we saw only one of the files had a hidden file in which we extracted.
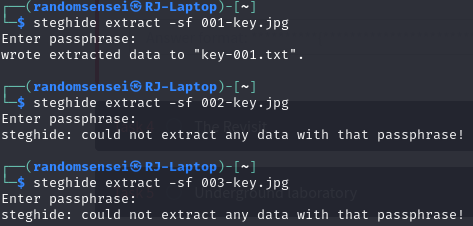
Now we will check exiftool to see if there is any important information given in the keys. Given that we already found a key in key-001 we will skip that file.
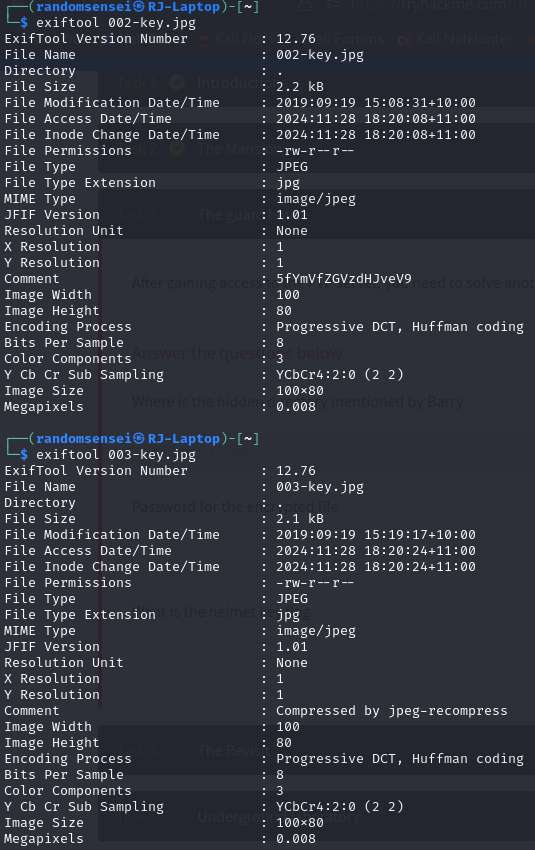
We find a comment with some text which we will extract to a new file. Now we will use binwalk to check if there is anything extra in addition to the image information.
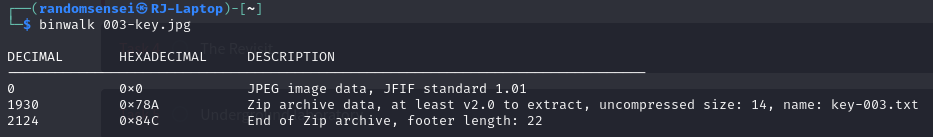
We see there is a zip in this image so we will unzip it cat there should be some text information.
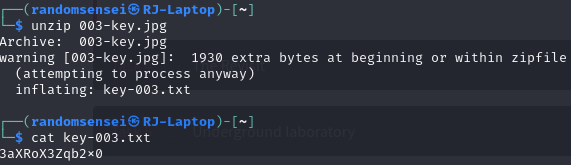
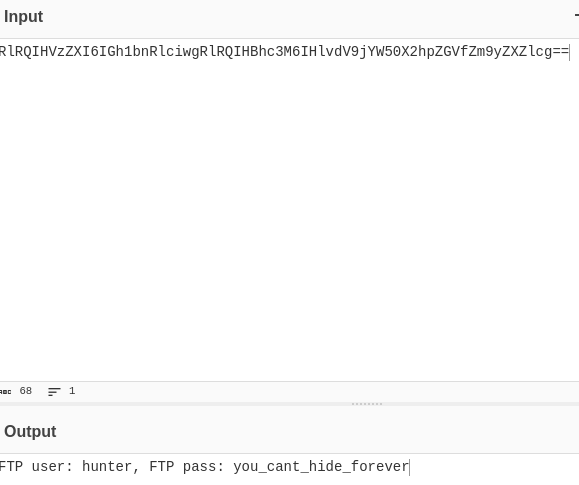
Adding all three keys together then decrypting using base64 we get:
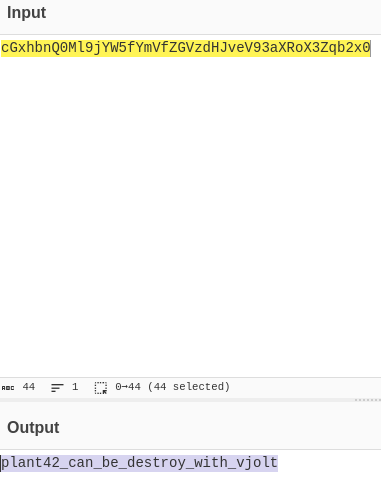
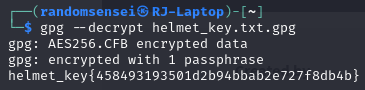
After decrypting the helmetkey file with gpg we receive:
Now going back to the closet room we can now enter the helmetkey:

In the Study Room we have a link which gives us a file called doom.tar.gz. Before we extract the file we will first check what is in the closet room:
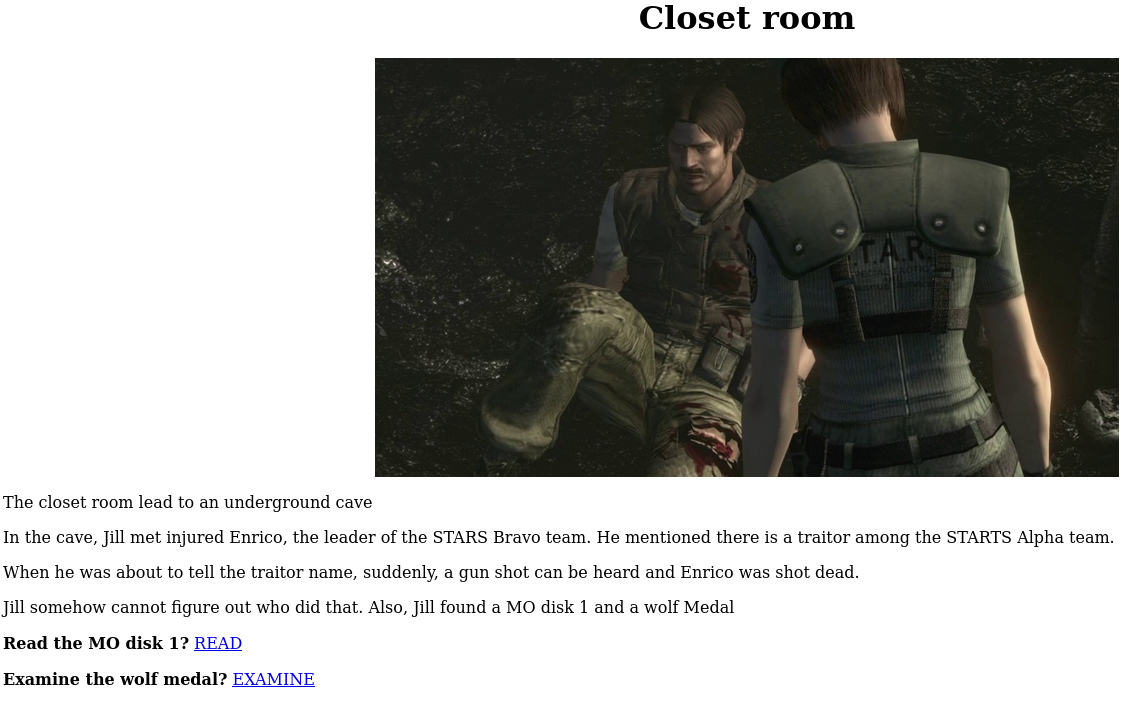
Here we have two links, once clicked we get:
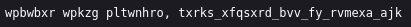
And:
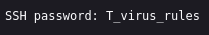
The above text looks like a vignere cipher, so we may need to look at the doom.tar.gz file first.
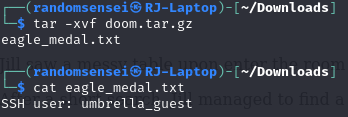
Now we have all of the ssh information we need but we also have the cipher to keep in mind. Now let's use ssh to connect to the server.
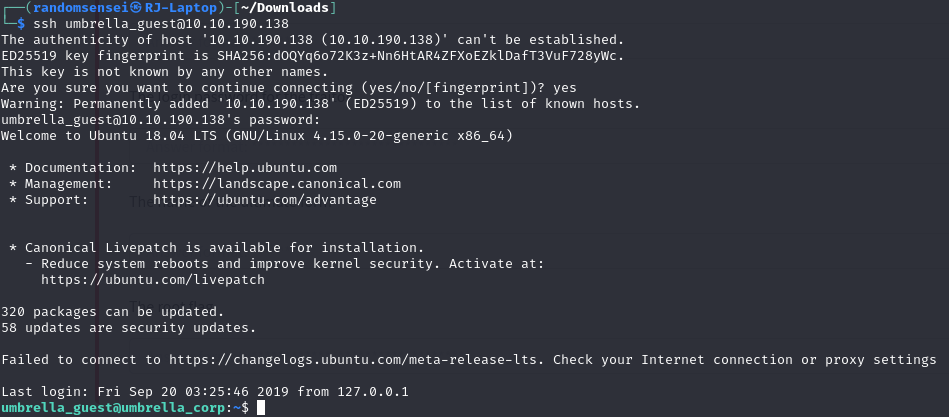
Now we will check the files and directories we can access:
There seems to be nothing there but we will list all of the files and directories using:
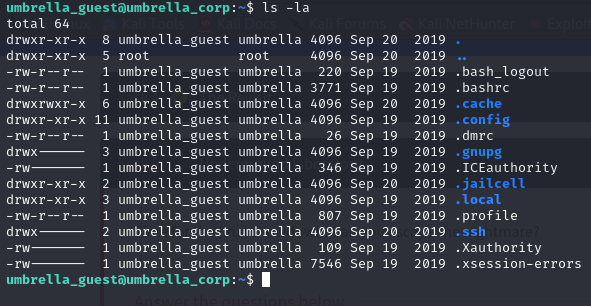
There is and interesting directory called .jailcell. Upon entering this we see some interesting information regarding chris.
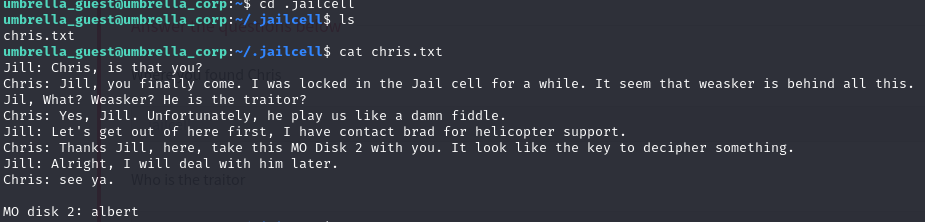
Now we have another name 'albert'. Now what if we use this name as the key for the vignere cipher that we found previously.
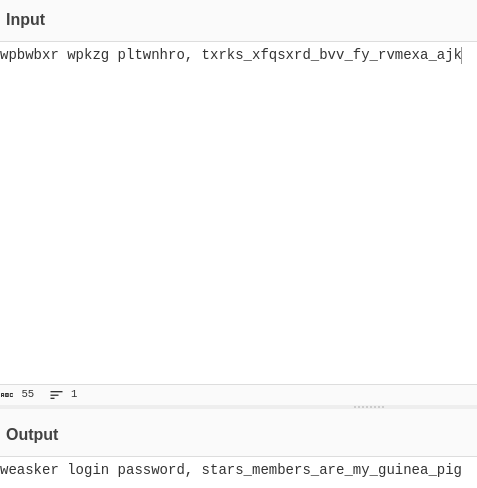
We now have the login for weasker, so lets ssh into weasker.
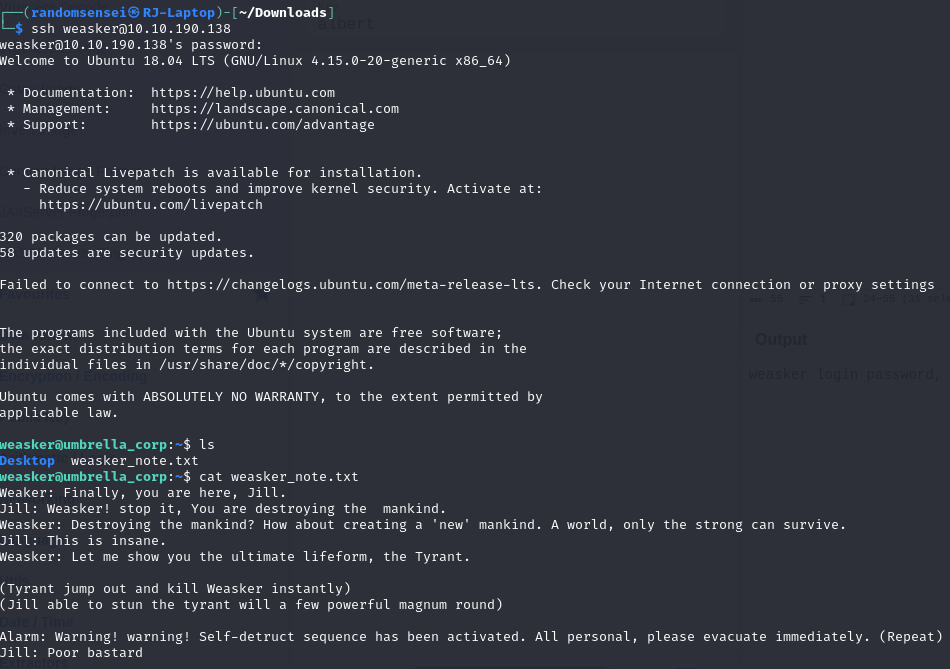
We have also found some interesting information. Now we with run sudo -l and we see that we can run any command with root.
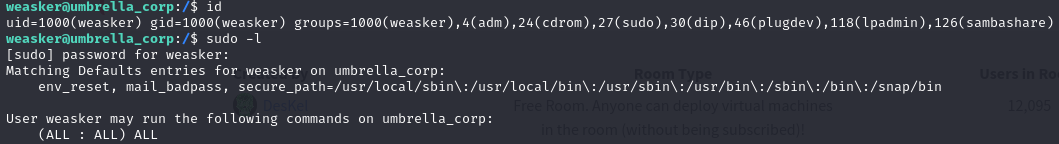
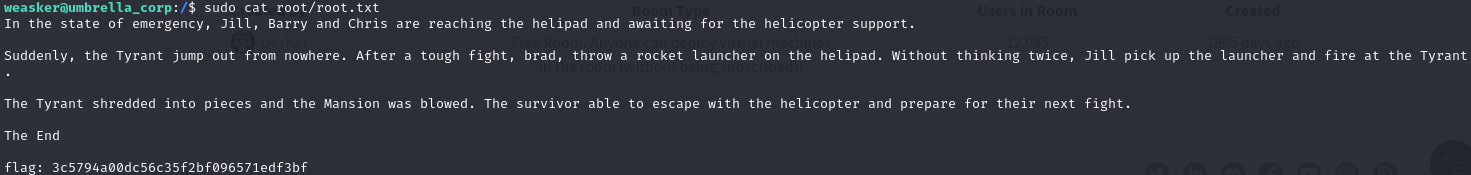
Now we will move into the root directory and find the root.txt.